As organizations face increasing pressure to demonstrate robust cybersecurity and privacy practices, the Health Information Trust Alliance’s Common Security Framework (HITRUST CSF) has emerged as a leading framework for managing risk, meeting compliance obligations, and providing customers with confidence in knowing their personal information and data are secure.
Developed in 2007 for the healthcare industry, HITRUST CSF now integrates multiple standards and regulations into a single, certifiable framework that supports organizations across various industries.
What Is HITRUST CSF?
The HITRUST CSF is a certifiable risk management and compliance framework that consolidates requirements from authoritative sources, including ISO, NIST, HIPAA, PCI and GDPR. It was designed to reduce the complexity of compliance by harmonizing these standards into a single, scalable structure.
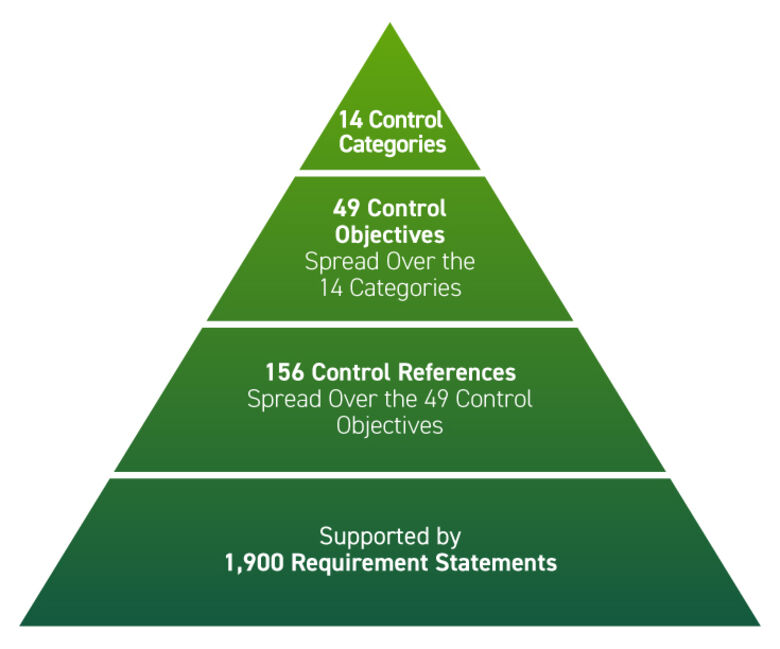
The framework is structured around 14 control categories, 49 control objectives and 156 control references, supported by more than 1,900 requirement statements. These are distributed across 19 assessment domains, including access control, vulnerability management and data protection.
The 19 assessment domains include:
- Information Protection Program
- Endpoint Protection
- Portable Media Security
- Mobile Device Security
- Wireless Security
- Configuration Management
- Vulnerability Management
- Network Protection
- Transmission Protection
- Password Management
- Access Control
- Audit Logging and Monitoring
- Education, Training and Awareness
- Third-party Assurance
- Incident Management
- Business Continuity and Disaster Recovery
- Risk Management
- Physical and Environmental Security
- Data Protection and Privacy
For a deeper dive into HITRUST CSF requirement statements, watch our HITRUST CSF: A Comprehensive Overview webinar recording.
What Is HITRUST CSF Certification?
HITRUST provides both assessments and certifications. Organizations can use assessments as an efficient way to address regulatory compliance, manage risks and identify gaps. On the other hand, HITRUST CSF certification — verified by an independent third-party assessor — enables organizations to prove their cybersecurity and privacy controls meet regulatory standards like HIPAA, ISO and NIST under one unified assurance framework.
Why Is HITRUST Certification Important? Benefits of HITRUST CSF
HITRUST is not just about checking boxes; it’s about building a culture of security and trust. The framework has been widely adopted in healthcare, but its reach extends far beyond. Financial services, higher education, retail and IT service providers are increasingly leveraging HITRUST to streamline compliance and strengthen their security posture.
One of the key advantages of HITRUST is the “assess once, report many” approach. Organizations can use a single HITRUST assessment to satisfy multiple regulatory and contractual requirements, reducing audit fatigue and improving efficiency.
Types of HITRUST Certification Assessment Pathways
HITRUST offers three certification options tailored to different organizational needs:
- e1 Certification focuses on foundational cybersecurity hygiene and includes 44 controls. It is ideal for startups or low-risk entities and is valid for one year.
- i1 Certification includes 182 controls and targets medium-risk organizations. It emphasizes leading security practices and is valid for one year.
- r2 Certification is the most comprehensive, with the number of controls determined by scoping factors. It assesses policy, procedure and implementation maturity levels and is valid for two years, with an interim assessment required.
Each certification level varies in effort, assurance and cost, allowing organizations to choose the path that aligns with their risk profile and maturity.
|
e1 |
i1 |
r2 |
|
|
Level of Effort |
Low | Moderate | High |
|
Level of Assurance |
Low | Moderate | High |
|
Assessment Cost |
$ | $$ | $$$ |
|
Number of Controls |
44 | 182 | Varies, ~300 Average |
|
Must Use Current Version |
Yes | Yes | No |
|
Maturity Levels |
Implemented | Implemented | Policy, Procedure, Implement — Req Measured & Managed — Optional |
|
Assessment Length |
~1 – 3 Months | ~2 – 3 Months | ~3 Months |
|
Certification Length |
1 Year | 1 Year Rapid Recertification (Year 2) | 2 Years Interim Assessment (Year 2) |
|
Target Organization |
Small Organizations Low Risk/Complexity Minimal Infosec Processes |
Medium to Large Organizations Medium Risks/Complexity Established Infosec Processes |
Large Organizations High Risk/Complexity Mature Infosec Processes |
HITRUST assessments evaluate organizations across five maturity levels: policy, procedure, implemented, measured and managed. Each level contributes a weighted percentage to the overall score. To achieve certification, organizations must meet minimum scoring thresholds across all domains. For example, the r2 certification requires a minimum score of 62% (out of 100%) per domain.
HITRUST Process: Timeframes and Readiness
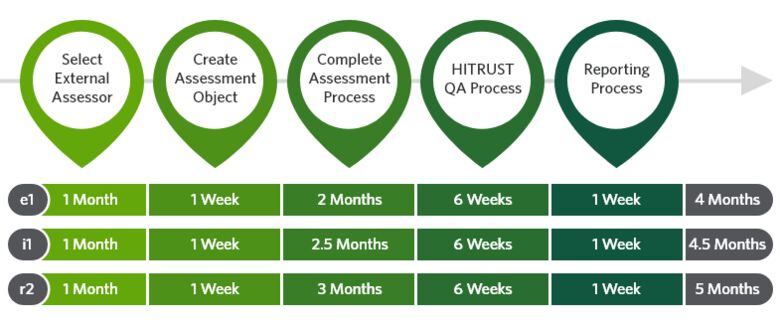 The time commitment for HITRUST will vary depending on the type of certification an organization is obtaining. The level of effort for each certification varies. Validated assessments must be completed within 90 days of fieldwork initiation. Remediated controls must operate for a minimum period — 60 days for policies and procedures, and 90 days for implemented controls — before they can be tested.
The time commitment for HITRUST will vary depending on the type of certification an organization is obtaining. The level of effort for each certification varies. Validated assessments must be completed within 90 days of fieldwork initiation. Remediated controls must operate for a minimum period — 60 days for policies and procedures, and 90 days for implemented controls — before they can be tested.
Organizations are encouraged to begin with a readiness or self-assessment to identify gaps and prepare for certification. The readiness process can take anywhere from six months to a year to complete, depending on the assessment type, to verify that all requirements are addressed in policy, procedure and implementation, with supporting evidence. The thoroughness of the readiness assessment directly affects the effort level required for the validated assessment.
Selecting an Assessor Firm for HITRUST Compliance
Using an external assessor is not only a requirement for obtaining a HITRUST certification, but choosing the right external assessor is a critical step in the journey. Authorized HITRUST assessor firms must meet rigorous criteria, including maintaining certified personnel and undergoing regular quality reviews. Organizations should evaluate potential partners based on their experience, methodology and industry focus.
Create Assessment Object
All HITRUST assessments require access to MyCSF, HITRUST’s SaaS platform. After purchasing a license, you’ll create your assessment object, which includes several steps:
- Naming and Security: Name your assessment, select your assessor firm, and grant access to external assessors and internal users.
- Admin and Scoping:
- Choose your assessment type (readiness or validated (e1, i1, r2)).
- Provide company background, customer base and security organization details.
- Define scope — systems to be certified, data locations (e.g., cloud, third-party) and outsourced services.
- Identify scoping factors such as record volume, geographic footprint, technical complexity and compliance requirements (e.g., HIPAA, privacy laws).
- Reservation: Schedule your quality assurance (QA) review. QA occurs after the 90-day assessment window, so plan accordingly.
HITRUST resources and your assessor firm are available to support you as you work through your assessment objective and respond to the questions.
Complete Assessment Process
This stage requires the most time, and how long it takes depends on which certification is being pursued, as shown in the table above. The following steps are involved:
- Evidence Collection
- Scoring and Validation
- Follow-ups
- Corrective Action Plans (CAPs), If Applicable
- Administrative Tasks
Scores are validated by your assessor, and progress can be tracked in MyCSF. If gaps exist, CAPs will outline remediation actions and timelines. Several administrative tasks, such as a representation letter, QA reservation, QA checklist and more will be required in this step.
HITRUST QA Process
HITRUST performs rigorous QA checks, including retesting and follow-ups, to ensure accuracy and quality. Multiple layers of review — from your assessor to HITRUST QA — help maintain integrity.
Reporting Process
After QA, HITRUST drafts and finalizes your certification report. This report is often shared with customers, partners and other third parties, so accuracy and completeness are essential.
HITRUST Security Framework FAQs
Below are frequently asked questions (FAQs) pertaining to the HITRUST CSF framework.
The cost to get HITRUST CSF certified varies depending on the size of your organization and the type of certification pathway you choose (e1, i1 or r2), with costs generally increasing for larger organizations and more comprehensive assessments. The required effort — lowest for e1, moderate for i1 and highest for r2 — and factors like infrastructure complexity and number of controls affect the overall cost.
Any organization that handles sensitive data, especially in healthcare, financial services, higher education, retail or IT, should consider HITRUST CSF certification to demonstrate robust cybersecurity and privacy practices. HITRUST is particularly valuable for organizations seeking to streamline compliance with multiple regulations and build trust with customers and stakeholders.
HIPAA is a U.S. federal law that sets mandatory standards for protecting electronic protected health information (ePHI) and applies to covered entities and business professionals in the healthcare industry.
HITRUST CSF is a certifiable framework that incorporates HIPAA requirements along with other standards (NIST, ISO, PCI, GDPR, etc.) into a single, comprehensive set of controls. While HIPAA is regulatory, HITRUST offers a broader, risk-based approach to compliance and security, enabling organizations to demonstrate adherence to multiple frameworks through a single certification (e1, i1 and r2).
HITRUST is a certifiable framework with mapped controls across multiple regulations (e.g., NIST, ISO), while a SOC 2 is an audit-based attestation focused on the AICPA Trust Services Criteria principles rather than a unified control set.
Your Guide Forward
As a HITRUST-approved external assessor firm, Cherry Bekaert’s Cybersecurity practice offers a comprehensive suite of services tailored to organizations pursuing HITRUST certification. With deep experience in IT audit, cybersecurity compliance and third-party attestation, we provide readiness assessments, validated assessments and advisory support.
Our team is comprised of Certified CSF Practitioners (CCSFPs) and Certified HITRUST Quality Professionals (CHQPs), who bring both technical knowledge and practical experience to the table, enabling you to navigate the complexities of HITRUST with confidence and clarity.
Related Insights
- Podcast: HITRUST 101: Understanding the Basics
- Webinar Recording: HITRUST CSF: A Comprehensive Overview









